Configure Tomcat To Use SSL/TLS Over HTTPS
In this tutorial we show how to configure Tomcat to use SSL/TLS over HTTPS. Secure Socket Layer (SSL), which now refers to the Transport Layer ouSecurity (TLS), is a protocol that encrypts the communication between the server and the client. These protocols are supported by all the major browsers and is the standard security mechanism to secure the communication between client and server.
Here is a short overview of what steps we need to take to enable SSL/TLS for Tomcat Servlet Container.
- Create Java Keystore for Tomcat.
- Create a SSL/TLS over HTTPS connector and assign/configure the new keystore.
- Optionally: redirect all traffic from HTTP to HTTPS.
- Run it, Test it and Verify it.
Generate keystore
We can generate a keystore using the Java keytool. The keytool is located in the %JAVA_HOME%/bin directory. We can optionally pass in a validity parameter, to make sure you don’t have to change the certificate every year. In particular, this certificate will be valid for 100 years. However, – because this is a self-signed certificate – most major browsers will not accept this certificate by default.
mnf:cert memorynotfound$ keytool -genkey -alias tomcat -keyalg RSA -keystore tomcat-keystore.jks -validity 36500 -keysize 2048
Enter keystore password:
Re-enter new password:
What is your first and last name?
[Unknown]: memorynotfound.com
What is the name of your organizational unit?
[Unknown]:
What is the name of your organization?
[Unknown]: memorynotfound
What is the name of your City or Locality?
[Unknown]: antwerp
What is the name of your State or Province?
[Unknown]: antwerp
What is the two-letter country code for this unit?
[Unknown]: BE
Is CN=memorynotfound.com, OU=Unknown, O=memorynotfound, L=antwerp, ST=antwerp, C=BE correct?
[no]: y
Enter key password for <tomcat>
(RETURN if same as keystore password):
Re-enter new password: Configuring Tomcat Connector
We created a new folder called cert in the %TOMCAT_HOME% directory, and placed the keystore inside. Next, we create a new connector for SSL/TLS over HTTPS. We configure this connector with the keystoreFile and keystorePass.
Open the %TOMCAT_HOME%/conf/server.xml.
<Connector
protocol="org.apache.coyote.http11.Http11NioProtocol"
port="8443" maxThreads="200"
scheme="https" secure="true" SSLEnabled="true"
keystoreFile="cert/tomcat-keystore.jks" keystorePass="password"
clientAuth="false" sslProtocol="TLS"/>Redirect HTTP to HTTPS on Tomcat
Make sure you have a connector listening on 8080 and redirects the traffic to 8443.
<Connector port="8080" enableLookups="false" redirectPort="8443" />Place this code in the /%TOMCAT_HOME/conf/web.xml file.
<security-constraint>
<web-resource-collection>
<web-resource-name>securedapp</web-resource-name>
<url-pattern>/*</url-pattern>
</web-resource-collection>
<user-data-constraint>
<transport-guarantee>CONFIDENTIAL</transport-guarantee>
</user-data-constraint>
</security-constraint>Demo
Because we redirected all HTTP traffic to HTTPS, we can browse to both: http://localhost:8080 and https://localhost:8443/ url and receive the same output.
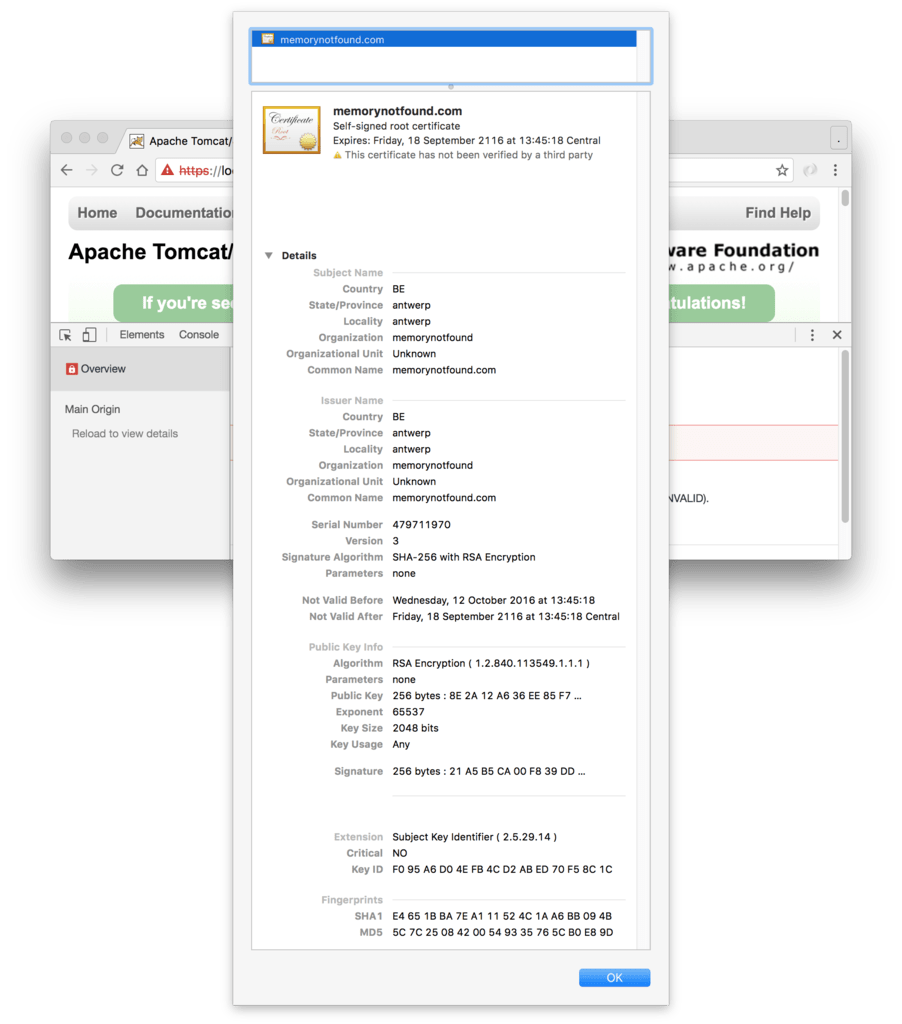
When we inspect the certificate, we see that the certificate is valid for over 100 years.